In today’s interconnected digital world, where data breaches and cyber threats loom large, traditional security measures fall short in providing adequate protection. Enter Zero Trust Security, a paradigm shift in access control that challenges the conventional notion of trust within networks. This comprehensive guide explores the concept of Zero Trust Security, its principles, implementation strategies, and its significance in safeguarding against evolving cyber threats.
Understanding Zero Trust Security
What is Zero Trust Security?
Zero Trust Security is a cybersecurity framework based on the principle of “never trust, always verify.” Unlike traditional security models that rely on perimeter-based defenses, Zero Trust operates on the assumption that threats could originate from both inside and outside the network. It advocates for continuous verification of trust for every user, device, and application attempting to access resources, regardless of their location.
The Core Principles of Zero Trust
Verify Every User: Authentication is required for all users, regardless of their location or network.
Validate Every Device: Devices attempting to connect to the network must undergo rigorous validation to ensure compliance with security policies.
Limit Access Privileges: Access controls are enforced based on the principle of least privilege, granting only the necessary access rights to users and devices.
Inspect and Log Traffic: All network traffic, both internal and external, is inspected and logged to detect anomalous behavior and potential threats.
Implementing Zero Trust Security
Zero Trust Architecture
Zero Trust Architecture encompasses a set of design principles and technologies aimed at enforcing the Zero Trust model across an organization’s network infrastructure. Key components include:
Micro-Segmentation: Dividing the network into smaller segments to limit lateral movement of threats.
Identity and Access Management (IAM): Implementing robust authentication and authorization mechanisms.
Network Segmentation: Creating zones of trust and enforcing strict access controls between them.
Encryption: Securing data in transit and at rest using encryption protocols.
Zero Trust Frameworks and Solutions
Several frameworks and solutions have emerged to help organizations adopt Zero Trust Security effectively:
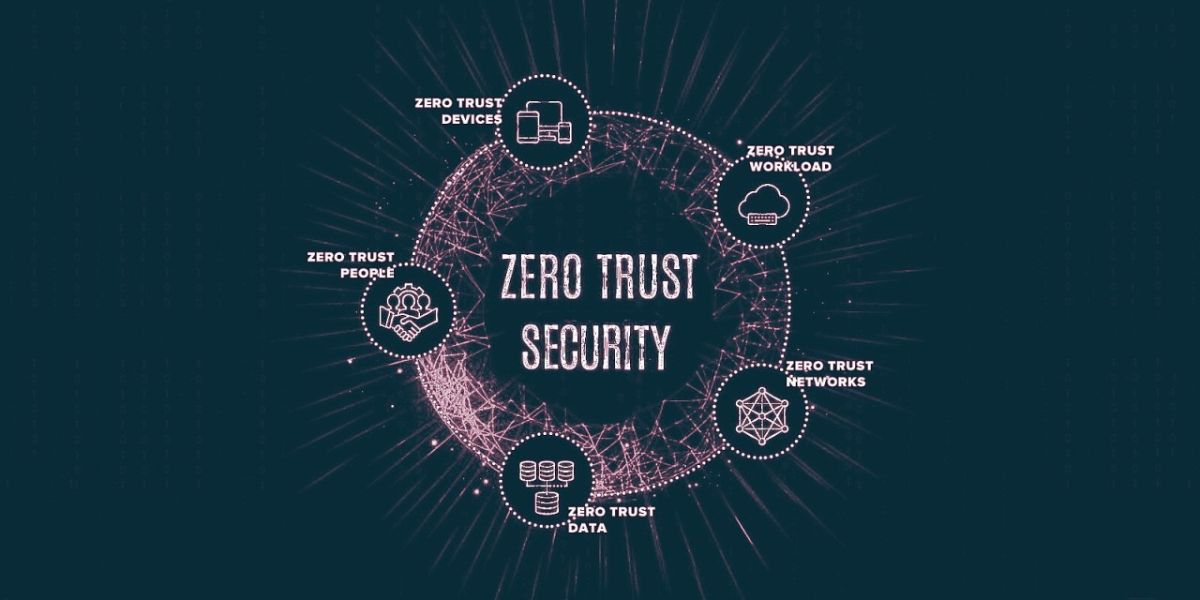
Forrester Zero Trust eXtended (ZTX) Framework: Provides a comprehensive approach to implementing Zero Trust principles across people, devices, workloads, and networks.
Software-Defined Perimeter (SDP): Offers secure access to applications based on user identity and device posture, without exposing the underlying network infrastructure.
Zero Trust Network Access (ZTNA): Delivers secure access to applications based on user identity and contextual factors, such as device health and location.
The Significance of Zero Trust Security
Addressing Modern Cyber Threats
In an era where cyber threats are becoming more sophisticated and pervasive, Zero Trust Security offers a proactive defense strategy. By assuming a “never trust, always verify” stance, organizations can mitigate the risk of data breaches and unauthorized access attempts.
Compliance and Regulatory Requirements
With data privacy regulations such as GDPR and CCPA imposing stringent requirements on organizations, implementing robust security measures like Zero Trust becomes imperative. By adhering to Zero Trust principles, organizations can demonstrate compliance with regulatory mandates and protect sensitive data from unauthorized access.
Final Words
Zero Trust Security represents a fundamental shift in cybersecurity philosophy, emphasizing continuous verification and strict access controls. By adopting Zero Trust principles and leveraging advanced technologies, organizations can bolster their security posture and stay ahead of evolving cyber threats in the modern digital landscape.
Commonly Asked Questions
Q1. What are the key benefits of implementing Zero Trust Security?
Enhanced security posture
Improved regulatory compliance
Mitigation of insider threats
Q2. How does Zero Trust Security differ from traditional security models?
Zero Trust operates on the principle of “never trust, always verify,” whereas traditional models rely on perimeter-based defenses.
Zero Trust emphasizes continuous authentication and access control, regardless of the user’s location or network.
Q3. What challenges might organizations face when adopting Zero Trust Security?
Legacy infrastructure compatibility issues
Cultural resistance to change
Complexity in implementation and management
Q4. Is Zero Trust Security suitable for all types of organizations?
Yes, Zero Trust principles can be applied across various industries and organizational sizes.
However, the implementation approach may vary based on specific business requirements and risk profiles.
Q5. How can organizations get started with implementing Zero Trust Security?
Conduct a comprehensive assessment of existing security posture and identify areas for improvement.
Develop a roadmap for implementing Zero Trust principles, considering factors such as organizational readiness, resource allocation, and technology investments.
Advertisement